Describe the Five Basic Attacks on Authentication Systems
Clone or borrow the credential - In this attack the credentials are duplicated and then used to log in. Clone or borrow is an attack that is usually done by shoulder surfing or.
5 Identity Attacks That Exploit Your Broken Authentication Okta
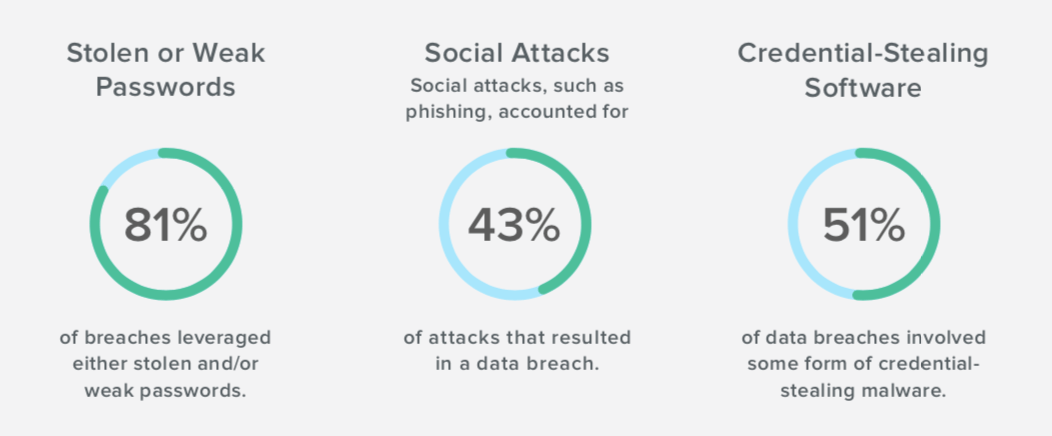
The 5 basic authentication attacks are Clone or borrow the credentials or token Sniff the credential Trial and error Denial of service DoS and Retrieve from a backup.

. Retrieve from offline - Extracting information from a USB or a. Describe the five basic attacks on authentication systems. 1000 Posted By.
It can also lead to personal. The five basic attacks on an authentication system are. Detects HTTP Basic authentication format string attack in user names and passwords.
R7Describe the five basic attacks on authentication systems. Describe the five basic attacks on authentication systems. Authentication attack is a serious type of hacking which can result into compromising entire IT infrastructure and software system.
Start your trial now. Describe the five basic attacks on authentication systems. Five Most Common Security Attacks on Two-Factor Authentication.
Following some high-profile password hacks companies like Apple Twitter and. Answers should be 3-4 paragraphs with a topic sentence that. The block from the account.
Describe the five basic attacks on authentication systems. First week only. Describe how password hashing works a.
Denial of service DoS - an attack with an intent of disrupting a. Trial and error - an attack wherein the malicious user attempts to determine passwords or access encrypted data. Describe the five basic attacks on authentication systems Offered Price.
Denial of services - blocking the user by either damaging the system or getting the user. 01032020 0920 AM Due on. Describe the five basic attacks on authentication systems.
Clone or borrow the credential or token - copy of the credential itself and uses it to log in. There are three main methods used for. 1Clone or borrow - attacker acquires a magnetic stripe readerwriter and copies mag stripe cards.
Sniff the credential - intercepts and. Compare and contrast human mistakes and social. Identify the five factors that contribute to the increasing vulnerability of information resources and specific examples of each factor.
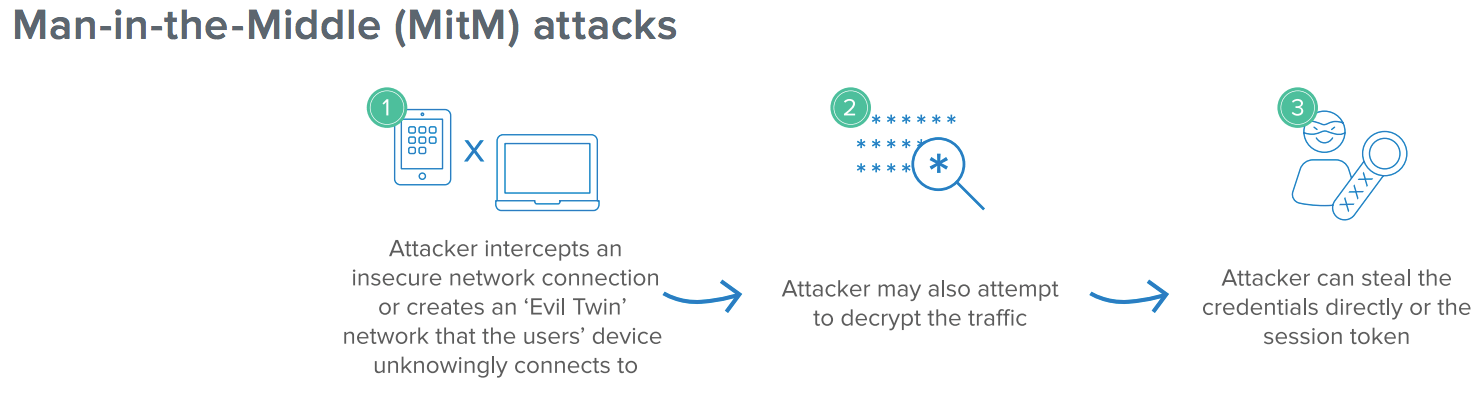
Write a basic C program in which a user enters the marks scored by. International Journal of Engineering Research Technology IJERT ISSN. Man-in-the-Middle MitM attacks A MitM attack on an organization is a highly targeted attack that can result in a full take of credentials and data-in-transit if executed.
Provide screenshots of using md5sum in your group VM under your account 5. Clone or borrow is an attack that is usually done by shoulder surfing or finding the login credentials and using those to log in. Solution for Describe an attack on a web cookie-based authentication scheme.
A threat agent could clone or borrow a users credentials or sniff the credentials that are being transmitted. The 5 basic authentication attacks are Clone or borrow the credentials or token Sniff the credential Trial and error Denial of service DoS and Retrieve from a backup. 2Sniff the credential -.
1 Issue 6 August - 2012 Protecting Biometric-based Authentication Systems against Indirect Attacks. Describe the five basic attacks on authentication systems Explain the difference between authentication and authorization. Token-based authentication technologies enable users to enter their credentials once and receive a unique encrypted string of random characters in exchange.
A type of brute force attack dictionary attacks rely on our habit of picking basic words as our password the most common of which hackers have collated into cracking dictionaries More. Authentication is the process that ensures the individual requesting access to a system website or application is the intended user. Answers should be 3-4 paragraphs with a topic sentence that restates the question and supporting sentences using the terms.

The Different Types Of Authentication Attacks What You Can Do To Protect Yourself Spam Auditor Blog
5 Identity Attacks That Exploit Your Broken Authentication Okta

Pin By Emilio Rr On Infosec Cyber Security Awareness Month Cyber Security Awareness Multi Factor Authentication
No comments for "Describe the Five Basic Attacks on Authentication Systems"
Post a Comment